On Friday, October 21, 2016, hackers unleashed a torrent of web requests at the Domain Name System (DNS) services managed by Dyn. By continually slamming these DNS servers with web traffic from different sources (known as "distributed denial of service," or DDoS), legitimate requests to get the IP addresses of popular sites like Twitter, Pinterest, Reddit, etc. were denied. What made this attack interesting is that the attackers relied on botnets (internet-connected computers that automatically communicate with each other to coordinate efforts) made of mostly IP cameras, home routers and printers infected with the Mirai malware.
Other home devices that might be connected to the Internet (and potential targets for other attacks):
- Smart TVs
- Cable receiver box
- Video game systems
- Thermostat
- Smart light bulbs
Mirai scans for connected Internet of Things (IoT) devices running some form of embedded Linux, including routers. It then attempts to "log in" to the device using some 60 known factory default usernames and passwords. Once in, Mirai infects the machine, turning it into a "bot" for use by the attacker and continues scanning for other connected IoT devices. The source code for Mirai was released in October. You can read about it here, but just be careful about clicking on random hacker site links.
With a knowledge of how Mirai did its dirty work, we can recommend a few ways to secure your internet-connected things to avoid becoming another bot on the net.
1. Unplug It
The best possible safeguard against hackers is to simply not have the device available for them. This means disconnecting it from the internet or, even better, turning it off completely. Unfortunately, this isn't always an option for some devices, like routers, that need to be on in order to blanket your home in warm, fuzzy internet access.
Kill Switch image by Stahlkocher. Courtesy of Wikimedia Commons
Here's a project idea: use a large button to control power to your router. Smash it when you get home or wake up to get internet and smash it again to turn it off when you leave. Maybe not the most convenient, but it denies access to your router (and, subsequently, the rest of your home network) when you're not using it.
2. Power Cycle
Another interesting aspect of some malware like Mirai is that it only lives in volatile memory (e.g., RAM). That means simply turning off the device and turning it back on again will rid it of the malware. Like the giant network kill switch from #1, you could make a simple microcontroller project to cycle the power on your IoT device every so often.
Image courtesy of Chris Evans
While that sounds great in theory, the problem is that your device is likely to get infected again within minutes, according to some reports. You're better off with a more permanent solution, like changing your default username and password.
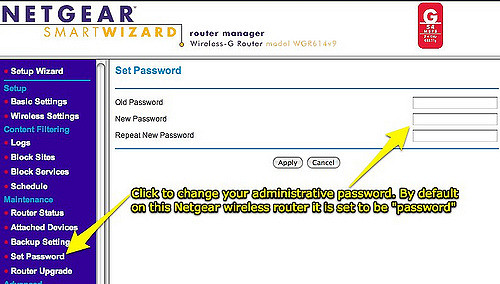
3. Change the Default Password
Seriously, if you do only one thing to secure your device, do this. It only takes a minute, and if everyone did it, Mirai would die pretty quickly.
Most home routers come with a default username and password like admin/admin or root/[no password]. Similarly, most internet-connected cameras have a web page that you can access to change such settings. If you are feeling particularly security-prone, go ahead and change the username too.
Image courtesy of Wesley Fryer
Oh, and please use a strong password. That'll help when the new-wave IoT malware hits, attempting to crack your device using a dictionary attack.
Need help configuring your router? How-To Geek has a great guide on doing just that.
I know some security people out there will yell at me, but I like to keep my username and password for my router written down on a piece of paper near the router (because I can never remember it). It's better than having it stored in Google Drive, and if an unfriendly hacker is in my house, I have bigger problems.
4. Update Firmware
Mirai and other similar malware hope that you've left your password set at default to work. However, it won't be long before we start seeing attacks that target IoT services and open ports as potential means for intrusion.
With more traditional operating systems, like macOS and Windows, users are regularly prompted to install updates that patch security holes. Many IoT devices left this feature out; they won't automatically check the manufacturer's site for new firmware updates. As a result, you, the user, are left to manually update whenever you see fit, which could translate to "never."
As smaller devices become more prevalent in our internet-connected world, they will become increasingly more interesting targets for hackers. Finding and fixing security holes is a never-ending game of cat-and-mouse, but you can stay ahead of the curve simply by checking for new firmware on a regular basis.
Want another project idea? Write a script that checks for new router firmware, automatically downloads it and sends you an email with it attached, reminding you to update your router.
The venerable Linksys WRT54G was highly regarded for its customizability
If you really want to dig into the weeds, you can try running custom firmware on your devices (assuming they support it). For example, I'm a big fan of dd-wrt. In theory, these alternatives give you increased control over security options, but they often have a much steeper learning curve.
5. Disable Universal Plug and Play (UPnP)
The idea behind UPnP was good: allow devices on your home network to discover each other, communicate and share files. However, it introduced so many holes that many security professionals recommend turning it off entirely.
The biggest security flaw in UPnP is that programs inside your network can automatically request port forwarding from the router. If one device on your network becomes compromised, it can open up ports to allow other malicious traffic to flow in and out of your network. This could leave computers and IoT devices in your network vulnerable to attacks from outside your network.
Luckily, fixing this is simple. While you are logged into your router (presumably changing the default password), look for a page with the label "UPnP" and disable any UPnP services. Unfortunately, doing this means you will need to learn how to manually forward ports, especially for things like online games.
Want to learn more about UPnP? Forbes has a good article explaining why it's a security risk.
(Update) Bonus: Disable Telnet and SSH
As pointed out by Member #398082, Mirai actually did its dirty work by trying to access a device through Telnet or SSH using default credentials. Changing the username and password in the web interface may help, but it doesn't necessarily guarantee that the the Telnet and SSH credentials get updated. If you can (likely through the same web interface used to change the password), disable Telnet and SSH services. If you can't, well, you might want to consider trading in the device for something more secure.
Being aware of potential security vulnerabilities in your network, especially as we begin to see more IoT devices hit the market, will help keep your devices from becoming the next zombie in a hacker's botnet (as well as keep your information safe!).
What other network and IoT security tips can you think of to help prevent another Mirai-style DDoS attack? Please share your ideas in the comments below.









Another idea is to use a better DNS provider. OpenDNS lets you block whole domains. For example, I have all of China blocked (*.cn) along with a number of other rogue nations. If you add the DNSCrypt extension, it provides security against man-in-the-middle attacks.
I work in this space (DNS) and it took me a moment to fully understand what you meant here. I suspect this confused some folks.
"Yes", you gain SOME protection if you configure your devices to use a filtered recursive (end user) DNS service, like OpenDNS. FYI - Dyn has a similar client DNS service with filtering (see "Dyn Internet Guide"). By using a filtered DNS resolver, you MAY prevent an already-infected device from "phoning home". But this isn't very effective, since it's trivial for the infection to SPECIFY a DNS resolver which isn't filtered, and still get the answer it needs to phone home. A 'dig' query with the -t or @ sign will do this.
Mainly: "no", your choice in DNS client/resolver service is not going to protect you from being exploited. It has no bearing on the success of the botnet compromising your IoT device. If it is vulnerable and exposed, the only fix is to make it not vulnerable or not exposed.
Leaving home-network credentials written down on paper at home is really not a horrible security idea.
Risk = likelihood * consequence. The likelihood of someone breaking into your house and exploiting your written-down credentials is quite low and the consequence if they do isn't that severe.
That's a different equation than the likelihood and consequence of someone exploiting written-down credentials at the office. And I still wouldn't leave banking credentials written down at home. The likelihood of a burglar finding them is low but the consequence is significantly higher than exploitation of IoT credentials.
Good point. Also, if they find the written credentials next to the routers, they've found the router and can just hard wire in. Having the written credentials doesn't really increase the consequences.
If writing it down allows you to have a stronger password, that is good.
Even better is a pseudo-random password based on something you have already memorized. Like the first or second letter of each word in a sentence, poem, etc.
Using a password manager (like LastPass) with the suggestion above is probably the best.
(And unrelated , but important security... : I have to plug using "two factor" on your critical accounts, like email. People can cause all sorts of havoc with your email, like resetting your bank or mortgage passwords in order to take control of them.)
My first added security item, isolate your IoT devices to a heavily controlled part of the network (I suggest VLANs, but there's probably better things out there). This way, if someone does get into the network via IoT, the rest of your network isn't compromised.
Use a better router than the ones you buy elsewhere. If you REALLY want to be secure on your network with your IoT of things you really need to build your router the way you need it to. I run a pfSense box at home and have it customized to only allow some specific ports to be opened and forwards to specific IP addresses (mostly consoles). pfSense, I found, to be one of the easiest and best custom built routers you can get (and they do updates all the time).
NOTE: The problem with UPnP is that Microsoft, Blizzard, Activision, DICE, EA, Sony, all use UPnP for their consoles/games to simplify the networking that needs to be done for games/apps they develop.
VLANs, routing, and proper firewalling (pfSense, Ubiquiti's EdgeRouter or USG, most anything in the Microtik world) are the ways to go. Trouble is, not everybody knows how to properly set those types of things up. (Given that you brought it up I'm assuming you're a fellow networking nerd; I know it's second nature for myself, but that's not any sort of assumption I'd want to cast on somebody else.) They also do cost a bit more than basic consumer-grade hardware (although the Ubiquiti EdgeRouter X is only $50), they also vastly out-perform them (1 Gbps routing, no big. The $100 EdgeRouter Lite can do 1 million packets per second too), are much more flexible in their configuration, and are updated routinely to boot. (Although you do need to apply it manually: ISPs don't like it when their gear auto-updates.)
Something not mentioned in the article, but worth doing if your firewall can support it: Outbound filtering. You should be able to block outbound traffic from your IoT devices and only allow it to communicate with white-listed networks/hosts and on white-listed ports. There's no reason most IoT devices should be talking on any port aside from 80, 443, or 53. (And even then 53 should only be to your internal DNS relay (router), so 80 and 443 to the outside world.) There's always the possibility of other ports in the case of specialized services, but I would recommend blocking the port (with logging enabled), then watching the firewall logs to see where it's trying to talk. White-list those destinations as you go until it's working properly. (Even better if vendors just list where their devices want to communicate so you can build the rules ahead of time and not feeling like you are missing anything.)
Definitely good point about the outbound filtering! Most home routers should be able to do this.
Yeah, I dabbled in the network stuff in college (and for IT positions also in college). My knowledge of that stuff is limited so I do a lot of Googling on proper things. I do know pfSense has a great book that you can buy that will tell you things in simple terms on what to do.
This is too hard for the average person. Hell, I know what you're talking about, and I wouldn't. If someone knows half as much as you and I do, they're already on top of default passwords and firmware updates - am I right? :)
The promise though is the next-generation of configurable routers (Google Wifi, etc) wwhich use "apps" to configure, will be able to do this. Getting the UI off the router (just make it an API appliance ) is going to be a huge step forward. You can put all the complexity in the app, and the router won't be exposed to the WAN ever (you could remotely manage via an app service, like the way Hue bulbs work). Much less risk.
This: "Want another project idea? Write a script that checks for new router firmware, automatically downloads it and sends you an email with it attached, reminding you to update your router."
I'd suggest a slightly different approach: "Write an IFTTT (if this then that) script that checks for new router firmware". Then connect YOUR script, to an existing IFTTT script which notifies you (email or text). Want to download it to dropbox, and email the attachment? There are IFTTT plugins for this already.
Whenever you want to do something that's 2 or more steps, take a look around to see what steps HAVEN'T been done by someone else already. :-)
That works, too. Thanks for the tip! :)
You have no idea what you're talking about. Mirai and other IoT botnets use default telnet passwords, which are hard coded in the firmware (i.e. the root passwords to the device). Changing the default password to the web interface has nothing to do with preventing your device being used in a botnet, it's about preventing strangers from looking at your camera feed or whatever.
So saying "if you do only one thing to secure your device, do this." is equivalent to saying "if you do only one thing, do nothing". Because changing your web admin password has nothing to do with changing the root password.
Thanks for the tip! I had (wrongly) assumed that changing the username/password in the web interface would update the credentials for all services, but it looks like many device manufacturers were enabling Telnet and SSH with hardcoded usernames and passwords (hopefully this practice stops...). I've added a section in the post about Telnet/SSH.
KrebsOnSecurity did a breakdown of vulnerable devices with some pretty good discussion.
There is some great app for password manager that will keep everything safe and easy to access instead of the little piece of paper near your router :P
thanks for the tips, I will double check tonight my router password and make it right.
I've seen the password manager for Chrome - is that the one you're referring to?
Google "LastPass" - and then look for reviews comparing it to other related PW managers (like Okta). From the reviews, you'll know which one is best for you.
Even for the browser, Okta is miles ahead of Google's password manager (which is already very good).
I'm not sure what Robomaniac was referring to specifically, but 1Password is outstanding, and is my preferred password manager.
yes, I mean 1Password for iOS device. I also tried minikeepass on ios that was good until I discovered 1Password.